Hi all, excited to share some of what we’ve been building and to introduce hypercerts to the ATProto community.
Where we started
The hypercerts project began at Protocol Labs with a simple goal: improve how we fund public goods. Many of the contributions society relies on most—open-source software, scientific R&D, and ecological regeneration—remain underfunded because their value is hard to see, coordinate around, and reward.
What are hypercerts
Hypercerts address this by serving as digital impact certificates. At their core, they capture structured claims about impactful work: who did what, when, and where. These claims can be enriched with additional evidence such as reports, measurements, and expert or community judgment. Funding mechanisms—grants, milestone payments, bounties, and retroactive rewards—can then be built on top. In this way, hypercerts form an open, shared, decentralized data layer for impact funding.
Switching to ATProto
Over the past months, we’ve been exploring ATProto as the infrastructure for this data layer. By now, we are convinced it’s the right foundation to build on:
-
Like posting on social media, value creators publish structured claims about their work.
-
Like replies, multiple evaluators can attach structured assessments.
-
Over time, projects accumulate a durable track record—made possible by the persistent, portable identifiers that ATProto provides.
Together, this enables a legible, interoperable impact graph that funding platforms can use.
What this unlocks
For projects and individual contributors, the goal is simple: remove as much friction from bureaucratic grant applications and other funding mechanisms as possible. Make it effortless to show your work and tap into (novel) funding mechanisms that reward the value you create.
For funders, the goal is equally straightforward: reduce the cost of due diligence, see the full context of a project’s work, enable better coordination, and allocate resources with greater confidence and transparency.
What we’ve built and experimented with so far
-
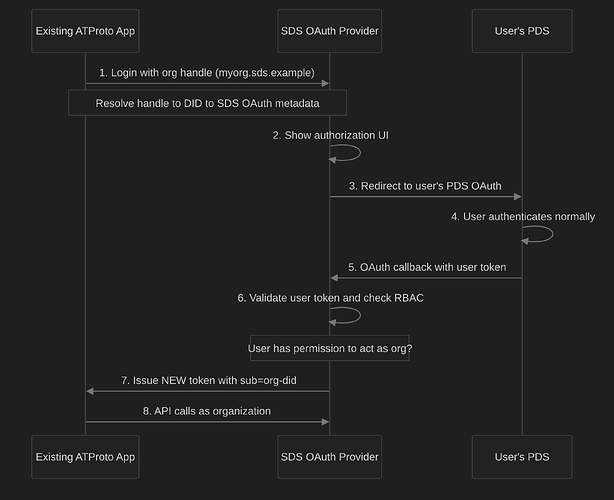
How can we represent an organization, where multiple users write into the same repo? For this, we extended the PDS into a Shared Data Server (SDS) to support multi-user org DIDs and corresponding multi-user repositories, with a lightweight access control model.
-
This is currently just a PoC; you can view it at https://github.com/hypercerts-org/atproto/tree/dev/packages/sds.
-
There is a demo frontend for testing the functionality at https://github.com/hypercerts-org/atproto/tree/dev/packages/sds-demo.
-
We have also extended https://pdsls.dev with support for writes on these multi-user SDS repos, and a new interface for exploring and interacting with the XRPC API; this can be seen at https://sdsls.dev.
-
-
How can we connect hypercerts on ATProto with blockchain-based impact funding mechanisms? For this, we have experimented with the wallet-proving approach by Stellz (https://piss.beauty/post/atproto-payment-identities)
-
How do we represent hypercerts in lexicons? For this, we’re iterating on lexicons to represent impact claims and evaluations in a clean, composable way: https://github.com/hypercerts-org/hypercerts-lexicon
Applications being built on top
Hypercerts is a protocol to allow multiple funding platforms to use the same schemas and data. We’re currently collaborating with Ma Earth and GainForest to build crowdfunding and collective funding platforms for regenerative land projects. These are our real-world testbeds for demonstrating how funding on hypercerts can work end-to-end.
We are excited to be here
We’d love to hear your thoughts, questions, feedback, pointers, etc. And we’re happy to share more about our work and learn from this community as we continue building.
If you want to dive deeper, here’s a recent blog post outlining our approach: https://hypercerts.leaflet.pub/3m6mnb2riz22o